By Jennifer Nieto, Best Card President
From the Fall 2017 Journal of the Colorado Dental Association
Every few months it seems like there are more revelations of large scale data breaches that expose the personal or financial information of millions of Americans. In 2017, there have been breaches involving Arby’s, Verifone, Dun & Bradstreet, Saks Fifth Avenue, Intercontinental Hotels Group, Chipotle, Kmart and Verizon that have resulted in credit card numbers or personal information being obtained by malicious characters.
The following graph, compiled by the Identity Theft Resource Center, a n
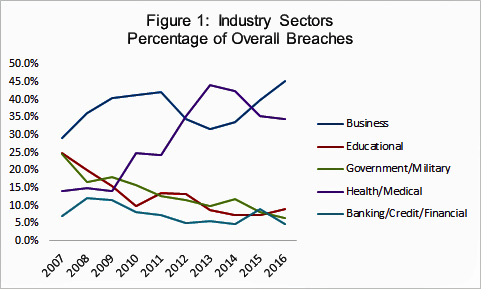
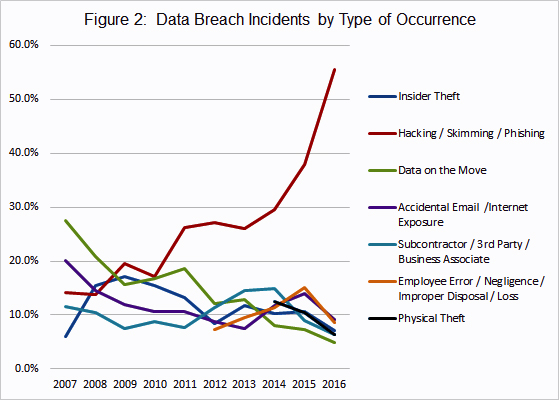
on-profit advocacy group, states that the healthcare industry is one of the largest targets for data breaches. By far the largest threats to data security are hacking, skimming and phishing.
- Hacking normally involves obtaining credentials to install malware that can monitor and extract sensitive information.
- Skimming is the process of attaching a physical device in the card processing environment to duplicate and steal the data.
- Phishing is the practice of sending fraudulent emails or phone calls purportedly from a reputable company to get individuals to reveal information such as passwords, personal information or credit card numbers.
To address these issues, the credit card industry has responded with a set of guidelines called Payment Card Industry (PCI) Compliance to ensure that any business that accepts credit cards has implemented secure procedures to protect transmission of card information. PCI Compliance is a requirement for any business that accepts credit cards, but the actual requirements that your business must meet is determined by the equipment and the method of communication used in processing.
As part of PCI Compliance, every business must complete an annual Self-Assessment Questionnaire (SAQ) unique to the processing environment. For example, a stand-alone credit card terminal that attaches over an analog phone line has a very simple SAQ that focuses on in-office procedures to protect credit card data. This is because the terminal encrypts all information at the point of entry and then sends the information over an analog phone line which is much more difficult than an IP connection for hackers to actively monitor. If your office uses a credit card processing terminal that connects over the internet or through your computers, not only will you have a more demanding SAQ that will ask about your network security, you will also be required to perform quarterly external PCI network scans to ensure that your network is secure from tampering.
PCI Compliance will usually be handled by your credit card processor even if they use an industry-approved PCI subcontractor. However, it is the merchant’s responsibility to make sure that their business has completed all the required steps to achieve compliance. While some credit card processors are very proactive in helping dental offices attain compliance, many don’t view it as their responsibility.
Having worked with thousands of dental offices for their PCI compliance, below are some helpful tips for any dental office to avoid PCI issues, maintain security and identify calls from scammers trying to get information.
- If your office stores physical credit card numbers, be sure to keep all card information locked up when not in use and to shred any card numbers once no longer required for business or legal reasons.
- If you have your office phones connected over IP (instead of analog phone lines), your router must separate phone activity from the rest of your office internet activity. While this should be common practice, many internet service providers such as Comcast, AT&T, etc. have not updated the firmware on the routers that they offer to businesses to be compliant with this practice. Currently you can receive a waiver for this vulnerability to achieve PCI compliance, but beginning Jan. 1, 2018, these routers will no longer be compliant without an update.
- Change passwords to systems if you have an employee leave. Former employees could login remotely and run fraudulent refunds to their own credit cards.
- Never store card numbers on a computer unless they are being stored in an encrypted format (where you cannot see the full credit card number) by a PCI approved software/gateway/processor.
- Be very careful when giving access to your passwords or allowing others to remotely login to your office computers. We have had offices that have called us after “Microsoft” called and said that they immediately needed to login to their computers. This is a common scam used to compromise your network and install malicious programs.
- We have had offices call us because “PCI” called and demanded to see a copy of their PCI scan report. Any PCI compliance steps would be handled in conjunction with your processor, there are no “PCI police” that would call you by phone. Giving away this information would essentially give a roadmap to hack your office network.
- There are many unscrupulous credit card processing companies that will call and say that your equipment or your network is not PCI compliant. They may even say that they need to do an “update” to your terminal and give you something to sign. Unless this call is coming from your credit card processor and they can provide your merchant number, this is an underhanded solicitation. The caller will have no information on the integrity of your systems unless you give it to them. These companies will try to scare you into signing a new agreement that usually has expensive costs and punitive contract terms.
- MasterCard has begun issuing credit cards that begin with a 2 (previously all MasterCards began with a 5) and some terminals need an update to accept these new cards. At Best Card, most of our terminals/online software systems auto-updated but we did have to re-download the VX520 terminals. MasterCard wanted these terminal updates completed by June 30, 2017, and can assess non-compliance fees of $2,500 per occurrence in the first 30 days, escalating to $10,000 in the next 60 days and up to $20,000 per occurrence for subsequent violations. That said, Mastercard will send a warning before assessing these fines. If you get sales calls saying you are non-compliant and may get fined, there might be some truth to this and you should check with your present processor.
Data security and PCI compliance are an ever-changing part of the business environment, but with reasonable preparations and updates it should be very manageable!
About the Author: Jennifer Nieto is the president of RJ Card Processing Inc, d/b/a Best Card. Best Card is the only endorsed credit card processor of the CDA, as well as over 25 other dental associations nationwide. If you have any questions about PCI compliance or the credit card processing industry, call 877-739-3952. They save the average dental office $1,860 (27% average savings) per year on their processing costs and offer excellent customer service. If you have a recent statement from your credit card processor and would like a detailed, no-obligation cost comparison, you can send the statement to CompareRates@BestCardTeam.com or fax to 866-717-7247.


